Network Penetration Testing for Cloud Environments
In an digital era where cloud environments have become the backbone of modern IT infrastructure, providing scalability, flexibility, and cost-efficiency, cybersecurity testing becomes more critical than ever. Network penetration testing is essential for securing cloud environments. It involves simulating cyber attacks to find and fix vulnerabilities. This proactive approach helps protect sensitive data and maintain a strong security posture. This article delves into cloud penetration testing, offering insights into why it’s vital
The Importance of Cloud Penetration Testing
As organizations migrate their data and services to the cloud, they face unique security challenges. Cloud penetration testing is designed to uncover vulnerabilities within cloud infrastructures that could potentially be exploited by attackers. Unlike traditional network environments, cloud services operate on a shared responsibility model, meaning that both the cloud service provider (CSP) and the customer must work together to secure the cloud environment. Therefore, penetration testing in the cloud is not only advisable but necessary to understand and mitigate risks associated with cloud computing.
Challenges in Cloud Network Security
Shared Responsibility Model
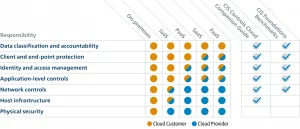
In cloud environments, security is a shared responsibility between the cloud service provider (CSP) and the client. CSPs secure the infrastructure, but clients must secure their applications and data. Misunderstanding this model can lead to security gaps.
Complex Network Configurations
Cloud networks are complex and dynamic, involving multiple layers and services. Managing security in such an environment is challenging, especially with multi-cloud and hybrid setups, which increase the attack surface.
Evolving Threat Landscapes
Cyber threats constantly evolve, targeting cloud-specific vulnerabilities. Keeping up with these changes requires continuous monitoring and proactive security measures.
Key Considerations for Cloud Network Penetration Testing
Effective penetration testing in cloud environments requires understanding cloud-specific challenges and nuances. Here are some key considerations:
Understanding Cloud Architecture
Cloud environments can be public, private, or hybrid, and they use different service models (IaaS, PaaS, SaaS). Each model has unique security implications and requires different testing approaches.
Compliance Requirements
Cloud environments must comply with regulations like GDPR, HIPAA, and PCI DSS. Penetration testing helps ensure compliance by identifying non-compliant configurations and vulnerabilities.
Dynamic Nature of Cloud Services
Cloud resources are dynamic, frequently changing. Continuous and automated testing is necessary to identify vulnerabilities in real-time.
Specialized Tools and Techniques
Traditional penetration testing tools may not be effective in cloud environments. Specialized tools designed for cloud security are necessary to address cloud-specific threats.
Network Penetration Testing Strategies
External and Internal Testing
- External Testing: Simulates attacks from outside the cloud environment, targeting exposed services and entry points.
- Internal Testing: Simulates an attacker who has breached the perimeter, focusing on lateral movement within the cloud network.
Vulnerability Scanning
Automated vulnerability scanners identify known vulnerabilities in cloud resources. These tools should be configured to understand cloud-specific assets and configurations.
Simulation of Sophisticated Attacks
Advanced tests simulate sophisticated attacks, such as zero-day exploits and advanced persistent threats (APTs), to assess the resilience of the cloud environment.
Detailed Testing Process
Reconnaissance
Gather information about the target environment, including publicly exposed services, IP addresses, and domain names.
Sample Code: Python Script for Subdomain Enumeration
import requests
from bs4 import BeautifulSoup
def get_subdomains(domain):
url = f”https://crt.sh/?q=%25.{domain}”
response = requests.get(url)
soup = BeautifulSoup(response.text, ‘html.parser’)
subdomains = set()
for row in soup.find_all(‘td’):
if domain in row.text:
subdomains.add(row.text.strip())
return subdomains
domain = “example.com”
subdomains = get_subdomains(domain)
print(f”Discovered subdomains for {domain}:”)
for subdomain in subdomains:
print(subdomain)
Scanning
Scan the environment for vulnerabilities using automated tools and manual techniques. This includes checking for misconfigurations, weak credentials, and unpatched software.
Sample Code: Using Nmap for Cloud Network Scanning
nmap -sS -p 80,443 -iL target_ips.txt –script http-enum
Exploitation
Exploit identified vulnerabilities to gain unauthorized access. Use a variety of tools and techniques to exploit weaknesses in cloud services.
Sample Code: Exploiting Misconfigured S3 Buckets
import boto3
def list_public_buckets():
s3 = boto3.client(‘s3’)
response = s3.list_buckets()
public_buckets = []
for bucket in response[‘Buckets’]:
acl = s3.get_bucket_acl(Bucket=bucket[‘Name’])
for grant in acl[‘Grants’]:
if grant[‘Permission’] == ‘READ’ and grant[‘Grantee’][‘Type’] == ‘Group’:
public_buckets.append(bucket[‘Name’])
return public_buckets
public_buckets = list_public_buckets()
print(“Public S3 Buckets:”)
for bucket in public_buckets:
print(bucket)
Post-Exploitation
After gaining access, try to escalate privileges, move laterally within the network, and exfiltrate data. This phase assesses the depth of the compromise and potential impact.
Sample Code: Extracting Data from Compromised Database
import mysql.connector
def extract_data():
conn = mysql.connector.connect(
host=”target-db-host”,
user=”attacker”,
password=”password”,
database=”sensitive_data”
)
cursor = conn.cursor()
cursor.execute(“SELECT * FROM confidential_info”)
results = cursor.fetchall()
for row in results:
print(row)
conn.close()
extract_data()
Reporting
Document findings in a detailed report, highlighting vulnerabilities, exploited weaknesses, and remediation recommendations. This report helps improve the organization’s security posture.
Advanced Techniques in Cloud Penetration Testing
Container Security
Containers are widely used in cloud environments. Penetration testing should include checking for vulnerabilities in container configurations, images, and orchestration tools like Kubernetes.
Sample Code: Checking Docker Container Vulnerabilities
docker scan my-container-image
Serverless Security
Serverless architectures introduce unique security challenges. Testing should focus on the security of functions, event triggers, and the overall serverless infrastructure.
Multi-Cloud and Hybrid Cloud Testing
Penetration testing should cover all cloud environments, including multi-cloud and hybrid setups. This ensures comprehensive security across different platforms and integration points.
Conclusion
Network penetration testing is crucial for securing cloud environments. It helps identify and fix vulnerabilities before they are exploited by malicious actors. Regular and thorough penetration testing ensures a strong security posture, compliance with regulations, and protection of critical data.
By using specialized tools and techniques tailored for cloud environments and continuously adapting to evolving threats, organizations can confidently leverage the benefits of cloud computing while minimizing risks.
————————–
Checkout Our Recent Posts: Click Here
Top 10 Cloud Security Interview Questions Finally Revealed!







