Wireshark is a packet analysis tool and is also used as a protocol analyzer. A packet is a data component that is sent over a computer network. When two or more devices communicate, a large number of packets are sent over a network and these packets can be captured for further analysis. Once these packets are captured, Wireshark allows us to inspect the contents of a packet, and monitor your network at a granular level. This becomes very effective in conducting a traffic analysis, which can be used to troubleshoot problems by locating the source.
Being a very powerful network sniffer, Wireshark is used popularly used by:
- Government Agencies
- Educational Institutions
- Non-Profit Organizations
- Small Businesses
Installing Wireshark on Linux:
sudo apt-get install wireshark
Wireshark is the most often-used packet sniffer in the world. Like any other packet sniffer, Wireshark does three things:
- Packet Capture: Wireshark listens to a network connection in real time and then grabs entire streams of traffic – quite possibly tens of thousands of packets at a time.
- Filtering: Wireshark is capable of slicing and dicing all of this random live data using filters. By applying a filter, we can obtain just the information you need to see.
- Visualization: Wireshark, like any good packet sniffer, allows us to dive right into the very middle of a network packet. It also allows you to visualize entire conversations and network streams.
Working of Wireshark
Wireshark is a packet sniffer and analysis tool. It captures network traffic on the local network and stores that data for offline analysis. Wireshark captures network traffic from Ethernet, Bluetooth, Wireless (IEEE.802.11), and many more. Wireshark provides the privilege of narrowing the results of captured packets by a large number of filters that are provided along with it. Each packet contains information such as the protocol used, source and destination IP and MAC, file content, etc.
Wireshark also colors the packet according to the protocol used, so that it becomes easier to identify the type of packet. Wireshark currently supports thousands of protocols. The majority of these are old and unpopular, but TCP, UDP, and ICMP are fully supported, allowing for the analysis of IP packets.

Capturing Data Packets
On opening Wireshark, we see a list of network interfaces that can be analyzed and monitored.
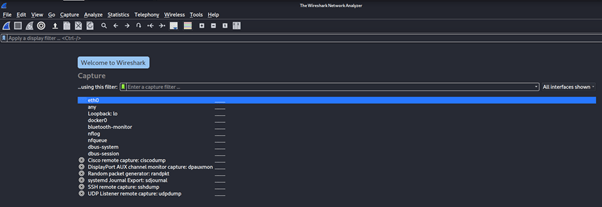
We can select one or more of the network interfaces using shift left-click. Once we select the network interfaces, we can start the capture.

Once we have captured all the packets you need, we use the same buttons or menu options to stop the capture. Best practice says that one should stop Wireshark packet capture before you do analysis.

Wireshark shows us three different panes for inspecting packet data. The Packet List, the top pane, is a list of all the packets in the capture. When you click on a packet, the other two panes change to show you the details about the selected packet. We can also tell if the packet is part of a conversation. Here are some details about each column in the top pane:
- No.: This is the number order of the packet that got captured. The bracket indicates that this packet is part of a conversation.
- Time: This column shows us how long after we started the capture that this packet got captured. We can change this value in the Settings menu if you need something different displayed.
- Source: This is the address of the system that sent the packet.
- Destination: This is the address of the destination of that packet.
- Protocol: This is the type of packet, for example, TCP, DNS, DHCPv6, or ARP.
- Length: This column shows us the length of the packet in bytes.
- Info: This column shows us more information about the packet contents, and will vary depending on what kind of packet it is.
Packet Details, the middle pane, shows us as much readable information about the packet as possible, depending on what kind of packet it is. We can right-click and create filters based on the highlighted text in this field. The bottom pane, Packet Bytes, displays the packet exactly as it got captured in hexadecimal. When we are looking at a packet that is part of a conversation, we can right-click the packet and select Follow to see only the packets that are part of that conversation.
Filters in Wireshark
Wireshark has the option of filters that eases our work by manifolds, there are two ways in which the filter can be applied:
- Right clicking on the packet
- Using the filter window at the top of the screen
Valid filter rules are always colored green. If we make a mistake on a filter rule, the box will turn a vivid pink.

To optimise our search we can use the below values :

For more blogs like this check our blog page







