Top 10 Cybersecurity Tools You Must Know
In the digital age, cybersecurity is no longer a luxury but a necessity. With the increasing number of cyber threats, professionals across industries need to equip themselves with robust cybersecurity tools to protect sensitive data and maintain the integrity of their IT infrastructure. Whether you’re an IT specialist, a business owner, or simply someone who values digital privacy, understanding the arsenal of cybersecurity tools available is crucial. In this article, we’ll delve into the top 10 cybersecurity tools you must know, including AI-powered solutions and essential cybersecurity monitoring tools.
Cybersecurity Landscape
Cybersecurity is a complex and ever-evolving field. As cybercriminals become more sophisticated, so too must the tools and technologies designed to thwart their efforts. The cybersecurity landscape is vast and varied, from firewalls and antivirus software to intrusion detection systems (IDS) and secure web gateways.
The Rise of AI Cybersecurity Tools
Artificial Intelligence (AI) has become a game-changer in cybersecurity. AI cybersecurity tools can analyze vast amounts of data to identify patterns and predict potential threats before they occur. These proactive capabilities are pivotal in staying one step ahead of cybercriminals.
Top 10 Cybersecurity Tools for Professionals
When it comes to selecting the top 10 cybersecurity tools, professionals have a wide array to choose from. Here are some of the top tools that should be on your radar.
1. Intrusion Detection and Prevention Systems (IDPS)
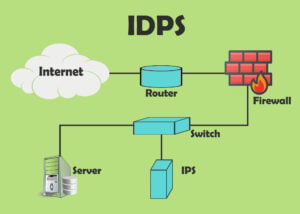
1.1 Snort
Snort is an open-source network intrusion detection system (NIDS) capable of real-time traffic analysis and packet logging. It can detect various attack signatures, including buffer overflows, stealth port scans, and more.
1.2 Suricata
Suricata is an advanced NIDS/NIPS engine with multi-threading capabilities, allowing it to efficiently process large volumes of network traffic. It supports deep packet inspection, TLS decryption, and file extraction.
2. Vulnerability Assessment Tools
2.1 Nessus
Nessus is a widely used vulnerability scanner that identifies potential vulnerabilities in your systems. It provides detailed reports, highlighting the severity of vulnerabilities and suggesting remediation steps.
2.2 OpenVAS
OpenVAS is an open-source tool offering comprehensive vulnerability scanning and management capabilities. It includes a vast database of known vulnerabilities, allowing thorough assessments of your network.
3. Security Information and Event Management (SIEM) Systems

3.1 Splunk
Splunk is a leading SIEM solution that collects, indexes, and analyzes machine-generated data in real time. It helps detect security threats, monitor network activities, and ensure compliance with regulations.
3.2 IBM QRadar
IBM QRadar is a robust SIEM platform that uses advanced analytics to detect and respond to security incidents. It integrates with various data sources to provide a unified view of your security posture.
4. Endpoint Protection Platforms (EPP)
4.1 Symantec Endpoint Protection
Symantec Endpoint Protection offers comprehensive security for endpoints, including antivirus, firewall, and intrusion prevention. It uses machine learning to detect and mitigate threats.
4.2 CrowdStrike Falcon
CrowdStrike Falcon is a cloud-based EPP that leverages artificial intelligence (AI) to identify and block advanced threats. Its lightweight agent provides real-time protection without impacting system performance.
5. Network Security Tools
5.1 Wireshark
Wireshark is a popular network protocol analyzer that captures and interacts with live network traffic. It helps professionals troubleshoot network issues and analyze security incidents.
5.2 pfSense
pfSense is an open-source firewall/router software distribution based on FreeBSD. It offers robust network security features, including stateful packet filtering, VPN support, and intrusion detection.
6. Penetration Testing Tools
6.1 Metasploit
Metasploit is a powerful penetration testing framework that helps identify, exploit, and validate vulnerabilities. It includes a vast library of exploit modules and payloads, making it an essential tool for security professionals.
6.2 Burp Suite
Burp Suite is a comprehensive web vulnerability scanner and penetration testing toolkit. It automates the detection of common web application vulnerabilities, such as SQL injection and cross-site scripting (XSS).
7. Password Management Tools
7.1 LastPass
LastPass is a secure password manager that stores encrypted passwords online. It generates strong, unique passwords for each account and automatically fills them in, reducing the risk of password-related breaches.
7.2 KeePass
KeePass is an open-source password manager that stores passwords locally in an encrypted database. It offers a high level of security with features like two-factor authentication and password generation.
8. Data Encryption Tools
8.1 VeraCrypt
VeraCrypt is an open-source disk encryption software that provides strong security for sensitive data. It supports hidden volumes and on-the-fly encryption, making it an excellent choice for protecting confidential information.
8.2 BitLocker
BitLocker is a full-disk encryption feature included in Windows operating systems. It encrypts the entire drive, preventing unauthorized access to data stored on the system.
9. Cloud Security Tools
9.1 AWS Security Hub
AWS Security Hub provides a comprehensive view of your security alerts and compliance status across your AWS accounts. It integrates with various AWS services to deliver centralized security management.
9.2 Microsoft Azure Security Center
Azure Security Center helps protect your cloud resources by providing advanced threat protection and unified security management. It uses machine learning to detect and respond to security threats.
AI Cybersecurity Tools You Should Know

AI is revolutionizing cybersecurity. Here are some AI-powered tools that professionals should consider incorporating into their cybersecurity strategy.
AI-Powered Threat Detection Systems
These systems use machine learning algorithms to detect anomalies that could indicate a security threat. By learning from historical data, they can identify even the most subtle signs of an attack.
Automated Security Incident Response
Automated incident response tools can take immediate action in the event of a detected threat, often without the need for human intervention. This rapid response can be invaluable in minimizing the impact of a cyber-attack.
Predictive Analytics for Cybersecurity
Predictive analytics tools use AI to predict and prevent future threats based on current and historical data. They provide actionable insights that can inform your cybersecurity strategy and resource allocation.
Ready to take your Cybersecurity skills to the next level?
Join our CSEP – Advanced Training Program and become a leader in AI-powered cybersecurity.
Click Here to Enroll CSEP Advanced Training Program
In Conclusion
Cybersecurity is an ongoing battle, and professionals must be equipped with the best tools to protect against threats. By understanding the cybersecurity landscape and implementing a range of AI-powered monitoring tools, you can significantly enhance your organization’s security posture.
Remember, cybersecurity is not a set-it-and-forget-it endeavor. It requires continuous attention and adaptation to the ever-changing threat environment. Stay vigilant, stay informed, and keep your cybersecurity tools sharp.
By prioritizing cybersecurity and investing in the right tools, you can safeguard your digital assets and maintain the trust of your clients and stakeholders. The tools mentioned in this article are just the starting point for building a robust cybersecurity framework that can withstand the challenges of the modern digital world.
Explore more related blog content for in-depth insights and expert tips on Cybersecurity. – Click Here







