In this article, we are going to read about ransomware. We are going to cover all the possible things about ransomware.
Content
- What is Ransomware ?
- How do Ransomware attacks work?
- Types of Ransomware
- Some Famous Ransomwares.
- Should you pay the ransom?
- How do you prevent ransomware attack?
What is Ransomeware ?
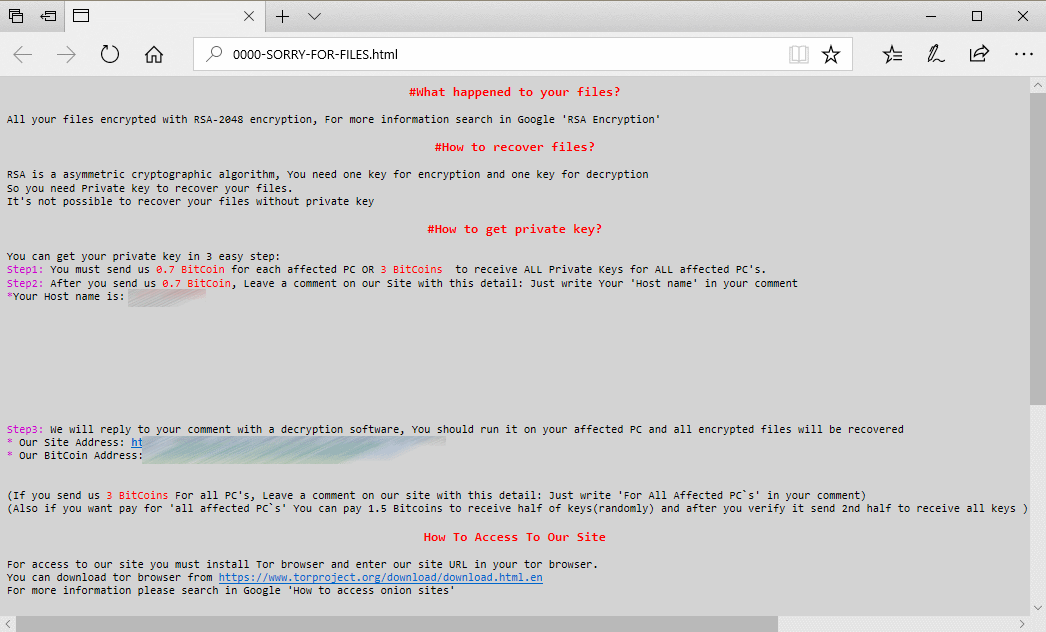
Ransomware is a type of malware in which the data of the victim is locked with typical encryption and ransom(money) is demanded to decrypt the data. The main motive of these attacks is money and unlike any other malware attack, In this victim is notified that they are compromised. The victims are given steps and instructions on how to recover the data. Usually, the payment is demanded in Virtual currency such as bitcoin.
Ransomware spreads through malicious attachments found in emails or infected malicious software and application like pirated software. They also spread from malicious external storage devices like pen drives, hard disks. Some attacks don’t even require user interaction to compromise the data.
How do Ransomware attack works?

Ransomware Kits are easily available on the dark web. Cybercriminals can purchase or rent the kit and perform attacks. Someone with little or no technical background can also perform this attack by just buying a kit. But, most cybercriminals create their own malware or modify the existing ransomware.
One of the common methods of delivering ransomware is through phishing emails. A malicious attachment is attached to the email and the mail is crafted so that the victim trusts the sender and click on the attachment. once the victim downloads the malware there computer and data are compromised.
There are more aggressive ways to spread malware. some aggressive ways are using a USB drive and spread is physical, browser plugins, chat messages, etc
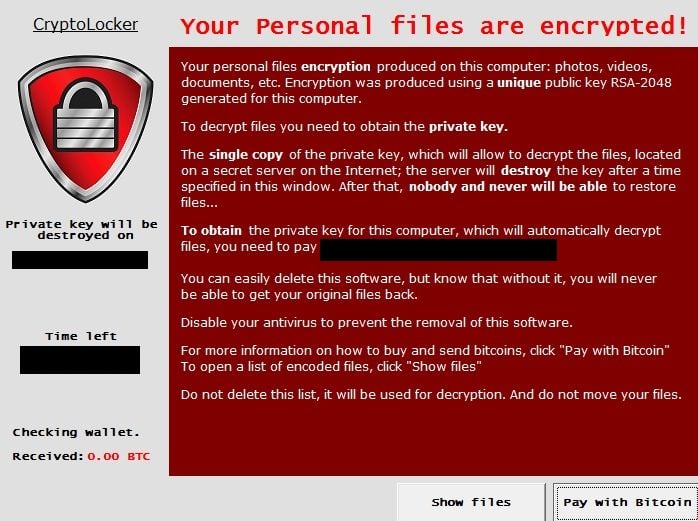
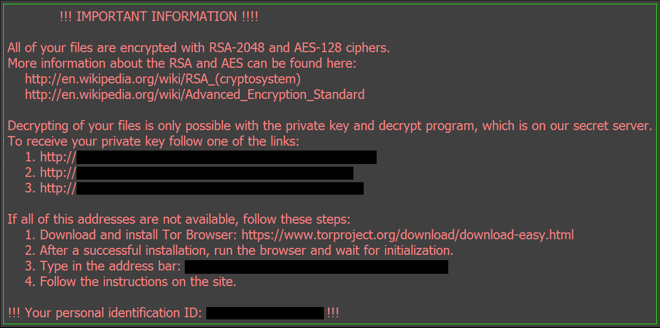
Once the malware is in the system, it will encrypt the victim’s data by adding extensions to the files and making them inaccessible. The encrypted files can only be decrypted using a key known by only the attacker. The ransomware then usually displays a message explaining the further steps to pay the ransom, where to pay, what will happen if they don’t. The attackers commonly demand ransom in bitcoins or any other cryptocurrency.
Types of Ransomware?
Ransomware is nothing but malware to extort digital currency from victims. An attacker can use several different ways to extort digital currency.
1. Scareware
Scareware is just low-level malware. the victims may receive pop-up notifications saying malware has been discovered. not responding to this malware will do nothing except pop up more notifications on your screen.
2. Screen Lockers
They are also known as lockers. these types of malware are designed to completely lock the victim out of their computer. When the victim opens the computer they will see a message with instructions on how to pay up electronic currency to open their own computer.
3. Encrypting Ransomware
These are classic ransomware and widely used one. Otherwise Known as a data kidnapping attack. In this, the malware victim’s data get encrypted and the victim has to pay up to decrypt the data.
4. Doxware
In this malware, the attacker threatens the victim to publish the data online if the victim does not pay.
5. Mobile Ransomware
This malware affects mobile devices. An attacker uses mobile ransomware to lock the mobile or mobile’s data and ask for the ransom to unlock the device.
Some Famous Ransomware
1. Ryuk

2. SamSam

3. WannaCry

4. Petya

5. TeslaCrypt

6. Crypto Locker
7. Locky
There is some old ransomware in this list but they are one of the most famous and destructive one. Some of them are still in use with modified versions.
Should you pay the ransom?
Most of the law enforcement agencies recommend not paying the ransom to these attacks because it will only give attackers encouragement to do more attacks like this. However when an organization faces the possibilities or no recovery or weeks of the recovery the thought of the lost profit may come into mind and then they began to compare the price of ransom to the price of data that is encrypted.
Paying up the ransom is not recommended for a number of reasons:
- Dealing with Criminals – There is no gaurantee that the attacker will really give your data back or decrypt it after paying up the ransom. According to kaspersky in 2016 20% percent of organizations payed up the ransom and still not get theeir files back.
- Potential Scareware – The ransom message may be used without accessing the organizations data just to scare.
- Possibilities of Repeated ransom demands – Cybercriminals will knoww that the organization has a history to pay up the ransom and this may rise up the chances of another attack.
You should always consider all the paths available before paying up the ransom.
How Do you prevent Ransomware Attacks?
- Backup Data regularly.
- Update all the softwares, including the antivrus.
- Train employees to avoid clicking links in email provided by stranger.
- Avoid Paying the ransom
- Dont’ put Unknown USB to computer
- Monitor the networks for any suspicious activities.
While ransomware attacks are impossible to stop so the organization must take all the precautions to protect their data from these attacks like Enforcing hard limits on who can access data, etc
That’s it for this article for more blogs like this please go to our blog page







