Introduction-
We know that security is a must in the Digital world . News reports about cyberattacks and data breaches leave no doubt that strong security is a must. But what’s the difference between information security, cybersecurity and network security?

When humans begin to keep secrets, that’s when information security came. In earlier days we used to keep physical files and folders , documents in key lockers. When digital world started using computers, network security started taking its form. It became important to protect the network security of digital systems. As soon as internet started growing in this business world, a new important industry called as cyber security takes a new form to protect data from unwanted threats.
So , as it is said , everything and everyone has its own importance, these three are equally plays a vital role in their areas. While the first two is just foe keeping information, data safe and secure, the third one “Cyber security” is important.
Closely related terms?
how do some of the industrialist define these terms let’s have a look
According to the SANS institute, Information security refers to the process and methods which are there to protect print, media and other form of private and confidential data from unauthorized use.

Cisco defines Cyber security as the practice of protecting networks, programs from digital attacks which destroys sensitive information.
Network security, the SANS Institute explains, is “the process of taking physical and software preventative measures to protect the underlying networking infrastructure from unauthorized access, misuse.
CIA Trio in Cyber security. What it is ?
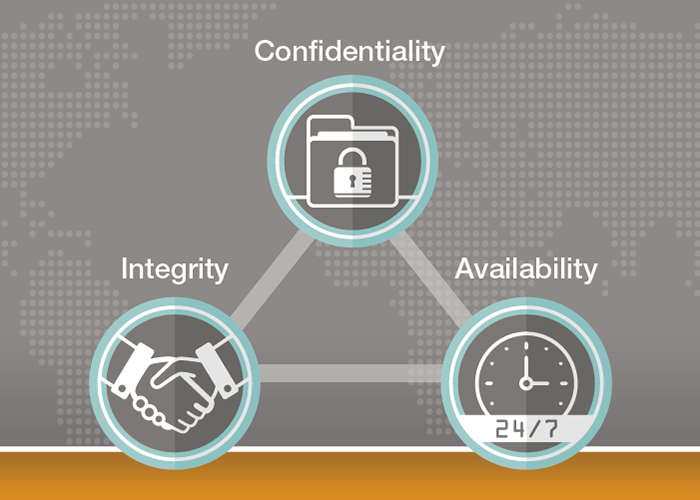
Whenever we are discussing about the three securities i.e. Information security, Cyber security, and Network security, we need to understand what is this CIA trio. What it comes to mind when hearing first about CIA trio? A secret group of three people? not exactly.
CIA trio refers to those policies and guidelines which the industry experts pay attention to while developing policies for effective information security system.
CIA trio is the most important aspects of Information security.
C- CONFIDENTIALITY : It protects the information from unauthorized access to people with the help of passwords, pin codes, ID’s and encrypted codes.
I-INTEGRITY: It protects the information from unauthorized access to people from being modified by unauthorized people. It safeguards accuracy of data.
A-AVAILABILITY- The information is available to people whenever they need them by keeping them with current updates and backups.
While observing throughout in security industry , The CIA TRIO according to Cybervie is to helps you to detect vulnerabilities of a system, attacks and manage emergency situations. It uses real time scenarios which can help students to understand the market and maintain its integrity. It is all time available to provide best cyber security training program.
Common risks-
Cyber Security:
- Social engineering
- Brute force
- Baiting
- Ransomware
Information Security:
- Access
- Destruction
- Availability
Network Security:
- Phishing. This type of online fraud is designed to steal sensitive information, such as credit card numbers and passwords.
- Computer Viruses.
Social Engineering
When cyber threat attackers your organization, they find about your business and employees. They know that employees outside of IT security are not aware of cyber threats, so they implement cyberattacks. Through the process of social engineering, threat attackers manipulate people to give them access to sensitive information.

- Phishing
In this form, cyber threat attackers gather the potential data with the help of email, phone, SMS chats.
- Man-in-the-Middle Phish Kits:
- Pretexting:
When a threat actor pretends to be an someone or have authority over it , they target people to do something which they would not do. - Baiting:
When threat attackers leave a system -poisoned device, such as a USB or CD at a place where people can find them, then if they use the infected device on their computer and by mistake install the software, threat attackers get their system access. - Quid Pro Quo:
When a threat attacker requests personal information in return for some kind of reward, e.g., money, free gift, or a free service.
How Does Cybersecurity Work?
- Application security: All of the platforms used within an organization provides a protective environment for data like aspects like architecture, code, etc.
- Data storage and transit: While data is at rest, it needs to be kept properly with appropriate storage and encryption.
- Disaster recovery: Both data backups and plans are necessary for keeping systems safe and running smoothly in the event of a hack.
- Mobile security: mobile security involves the steps and policies to protect the systems and the information.
- Identity management: It ensures that only authorized users can access data.
- Training: Users must also know how to use devices safely and identify and report malicious attacks or suspicious events just like Cybervie providing exclusive training programs related to cyber security.
Network, info and Cyber: Can information in these security systems overlap?
When digital data was a relatively new concept, it was easy to distinguish InfoSec, cybersecurity, and network security. As usual, cybersecurity took on the role of data protection. Most professionals understand the technology behind you, but the information security umbrella tends to place more emphasis on data testing, such as prioritization and risk.
For each type of security, many experts use the CIA triangle, which refers to confidentiality, integrity, and access to data. While they may use different methods, InfoSec, cybersecurity, and network security all aim to protect CIA employers from data security. Indeed, because network security is part of cybersecurity, which is part of information security, these three have significant differences.
Meaning of cloud and network security.
what is a hybrid cloud?
Both Cloud and Network security aim to prevent any data and ensure that the information is not changed. The role of both cloud and network security is to protect the organization’s IT infrastructure from all types of cyber threats, including:
- Ransomware
- Insider attacks
- Malware like viruses, worms, and Trojans
- Zero-day attacks
- Tradecraft attacks that bypass normal technical controls
- Denial of service attacks
Conclusion-
We visualize the world, which owns businesses in cloud storage. This brings us to the need for Cyber Security and Network Security. Cyber Security is a field in which we protect our data from cyber criminals. Cyber-security refers to the use of computer network software, software, or other technologies to protect online threats. Maintains a set of processes used to protect the integrity of networks, programs, and data from unauthorized access. Lock network (Network security). Network security is a subset of Cyber Security aimed at protecting networks.
I hope we have learnt enough about what is the difference between closely related terms Cybersecurity, Information Security and Network Security.






