In this article, we are going to see about session hijacking attacks and how they are done.
What is session hijacking?
Session hijacking also known as cookie side-jacking is an exploitation of a valid computer session. It is another form of Man-In-the_middle attack which gives the hacker full access to the online account.
It is an attack where the user’s session is taken over by hacker.
You must be wondering what is session?
Basically session a time when two computers communicate with each other to make a connection. Communication can be a computer-to-computer or client-to-server. A session is started when you login to a service.
Like when you log in to Facebook, Twitter, Instagram, or any other website, it creates a ‘session cookie’, it is a piece of data that identifies the user for the server.
As long as the session token is there the server will allow the user to use the application.
The session hijacking attack relies on the attacker’s knowledge of your session cookie. If the attacker has your session cookie they can use your account to do all sorts of things.
How session hijacking works
For a successful attack, the attacker must have a session ID of the victim.
1. Malicious link

The hacker can steal the session ID in many ways, some of them are hackers can make the victim click on the malicious link which is loaded with a script that will copy your Session ID or session cookie and send it to the attacker.
2. Cross-site scripting(XSS)
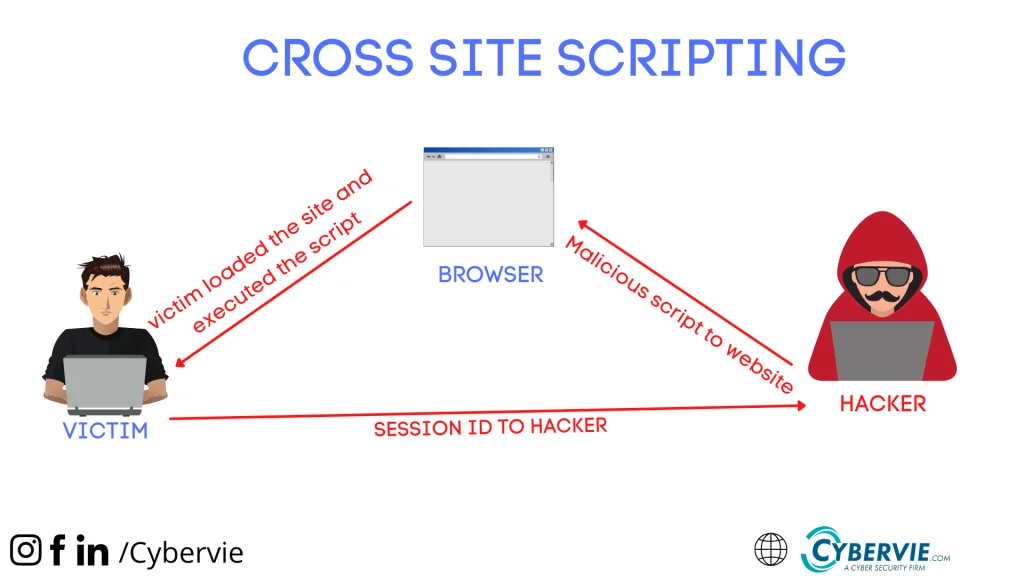
With cross-site scripting, With the help of XSS, the hacker forces you to run a script on your computer that will copy the session ID/Cookie and send it to the hacker.
3. Session sniffing

In session sniffing the attacker sniffs or capture all the packets and cookies between victim and website. And extract the session ID of the victim to use it to authenticate with the server and use the victim’s account.
4. Bruteforce attack
The attacker can blindly just brute force the Session ID, and if any of the ID matches with the website server, The hacker can use the account on the server. Hackers can do all sorts of bad things using this account. Basically, it’s just a try-and-run case if a hacker is lucky enough he will get a session ID.
Session Hijacking Tool
Let’s see some tools.
Here we are providing only the list of tools.
These are some of the best tools you can use for session hijacking.
How to prevent Session Hijacking
- Use HTTPS to ensure SSL/TLS encryption of all the session traffic. From this, the attacker can’t see the plain text session ID.
- IPSEC, SSL, SSH encryption can help to prevent network level session hijacking.
- Use VPNs when surfing an unencrypted site.
- Avoid log in on unencrypted websites.
- Be aware and always scan your network for vulnerabilities.
Frequently Asked Questions.
Q1. Is session hijacking a type of phishing?
Ans. No, basically session hijacking is not a type of phishing attack. It is a type of spoofing or you can say MITM attack.
Q2. Does SSL protect from session hijacking?
Ans. End-to-End Encryption and the web browser using secure HTTP or SSL always prevent unauthorized access to the Session ID.
For more content like this see our blog page.







