Demystifying DFIRaaS: A Buyer’s Guide to Choosing the Right Incident Response Solution
Nowadays, technology and the world of the Internet have escalated to a new level, requiring us to be extremely conscious of the possible dangers that may arise due to the digital space, and cybersecurity policies and measures are keys to this. With continuous cyber disruptions being the new normal, having a reliable incident management solution becomes a key challenge. I see it as a significant part of all cybersecurity strategies. It is, thus, vital to come up with incident management plans for better handling.
Understanding Incident Response Solutions
You might want to get a good grip on what the solutions basically aim to achieve. The security breach management system is, in particular, a structure that creates a procedure for identification, management, mitigation of security breaches and covering inefficient cyber threats.
What Is DFIRaaS?
‘DFIRaaS is a query-based service that provides organizations with a team of experts and a suite of tools that are ready to respond to and investigate cybersecurity incidents.’
Opting for this type of service ensures that businesses of all sizes will be equally protected and have the same know-how in comparison to large entities having their teams specialized in the certain field that is.
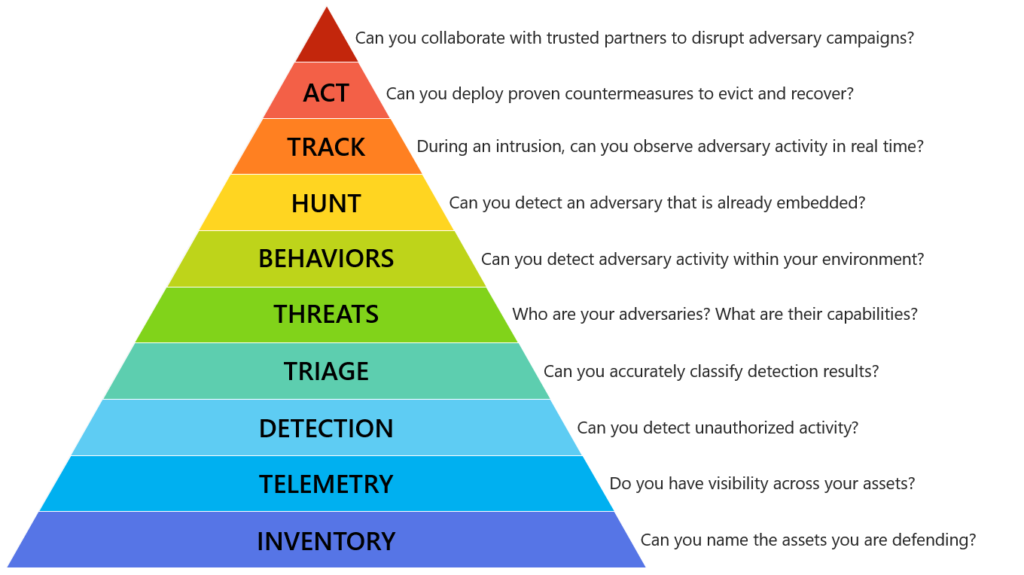
Hierarchy of DFIR
Why Choose DFIRaaS?
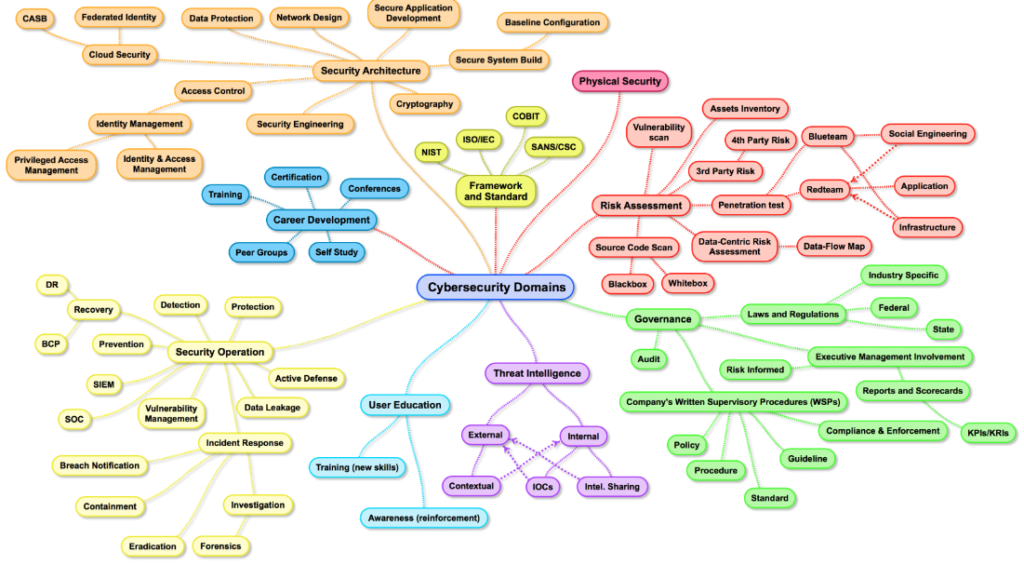
Where you have lot of options in Cybersecurity, Choosing DFIRaaS should be carried out because of the following advantages
- Expertise on Demand: You have the advantage of the immediate experience of cybersecurity experts in digital forensics and incident response.
- Cost-Effectiveness: It is usually less expensive than employing a full-time in-house team, especially for small to medium-sized businesses.
- Scalability: Using DFIRaaS can be an option of scaling your business that may respond to your organization’s needs either to a single incident or to multiple, ongoing threats.
- Continuous Improvement: It is usual for providers to always use their tools and methodologies to the changing threat landscape to be always up to date.
Key Factors to Consider When Choosing a DFIRaaS Provider
Selecting the right DFIRaaS provider is a critical decision that can affect your organization’s ability to respond to and recover from incidents. Here are some of the most important factors to consider:
Experience and Expertise
The provider’s track record is what matters most, of course. Therefore, you should be looking for a team with a previous record of the successful handling of incidents similar to those your organization may face. Their expertise in various industry sectors and their understanding of emerging cybersecurity trends and tactics should also be present.
Services Offered
It is of absolute importance to get a complete picture of the services that the provider will supply. A broad DFIRaaS solution will, not surprisingly, include but certainly not be limited to the following:
- Threat Detection and Monitoring
- Incident Investigation and Analysis
- Digital Forensics Services
- Containment and Mitigation Strategies
- Recovery and Post-Incident Support
Response Time
Well, in the world of threats cyberspace, time is a critical resource. Make sure that the provider promises quick turns around whether it is for a single page or a complete document. When an event is identified and action is taken promptly it has minimal chance of inflicting harm.
Communication and Collaboration
The rules of communication are equally important during a security breach. When engaging the services of your preferred DFIRaaS provider, he/she should be able to integrate with your team and ensure that everyone is informed throughout the process.
Customization and Integration
The incident response solution that you choose should readily meet the needs of your organization and should also be compatible with all of your current security systems and programs. It is crucial to avoid categorizing because the process does not often work in a generalized manner in the context of cybersecurity.
Compliance and Regulatory Requirements
Make sure that the provider of the DFIRaaS is aware and follows all the standards and regulations that apply to your business model. This is important especially for conserving your privacy in addition to legal implications as well as the legal consequences that you may be subjected to.
Evaluating DFIRaaS Providers
When evaluating potential DFIRaaS providers, consider the following steps:
Request Case Studies and References
The testimony of the current and former users can be another source of information about the performance and reliability of the providers.
Assess Their Tools and Technologies
The primary aim of the best DFIRaaS providers is to use advanced tools, such as threat intelligence, forensic analysis and incident management.
Understand Their Methodology
It is important for the incident that the provider uses in their response plan to be well defined, organized, and founded on tried and tested techniques. Learn how they manage the cycle of incidents, including threat identification, prevention, containment, investigation, and prevention after an occurrence.
Check for Continuous Monitoring and Proactive Threat Hunting
Constant surveillance and proactive approach to threat detection are critical to identifying potential threats before more damage can occur. Use the following steps to confirm that the identified provider integrates the services with DFIRaaS.
Consider Their Industry Specialization
Some DFIRaaS providers may specialize in certain industries, such as finance, healthcare, or retail. If your organization operates in a sector with unique security challenges, a specialized provider might offer the most effective solution.
Making the Decision
Cost vs. Value
Although the cost is one of the vital factors, the value the service will give back is unavoidable. Low-cost and more affordable ones might not always have the complete coverage and specialized skills that are necessary for your organization.
Long-Term Partnership
Choose somebody from the provider side that you can actually partner for a long time. Incident response will not do the job once but it should be a continuous need. You need to pick a company that goes hand-in-hand with your organization in terms of growth and adaptation.
Service Level Agreements (SLAs)
Go through the SLAs in detail to understand what is assured in relation to response times, availability, and support options. Make sure that the SLAs are in line with your organization’s expectations and requirements.
Conclusion
Identifying the right DFIRaaS provider is one of the most vital in making decisions if your organization is to be ready for tackling any cyber threat. If you take your time about it and put some careful thought into thinking about what it is that you need and what options are out there, expertise, service, and reaction, then you will be making the right decision for your cybersecurity
Incident response is well understood and highly valued by the Cybervie team, as it often involves conflict. The services offered under our DFIRaaS umbrella are standalone, each one offering full-spectrum support, including threat identification, analysis, and remediation. Our team of experienced and well-trained specialists, as well as the utilization of specialized software tools, allows us to create personalized solutions to address the needs of your sector.
======================================================
Check out our DFIRaaS Service: Click Here
======================================================